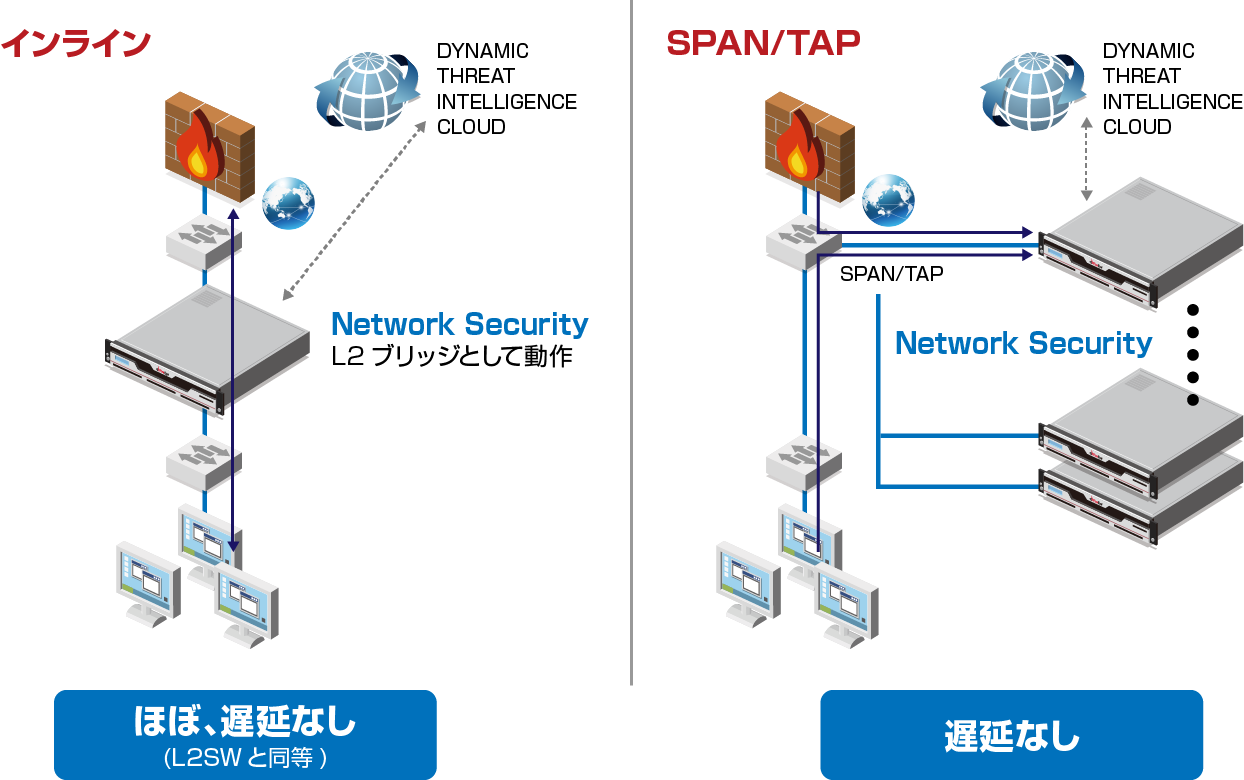
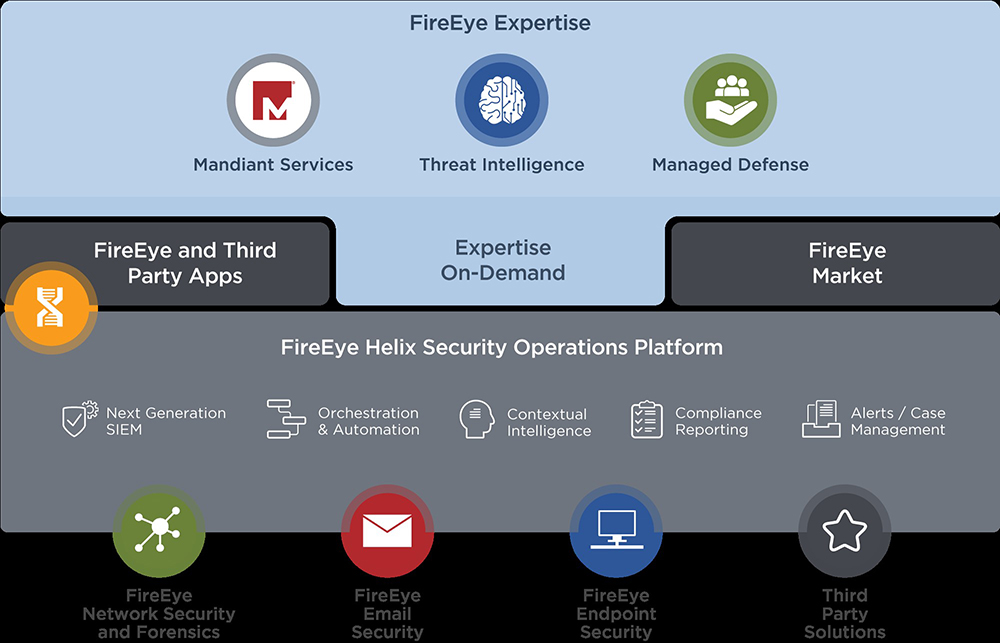
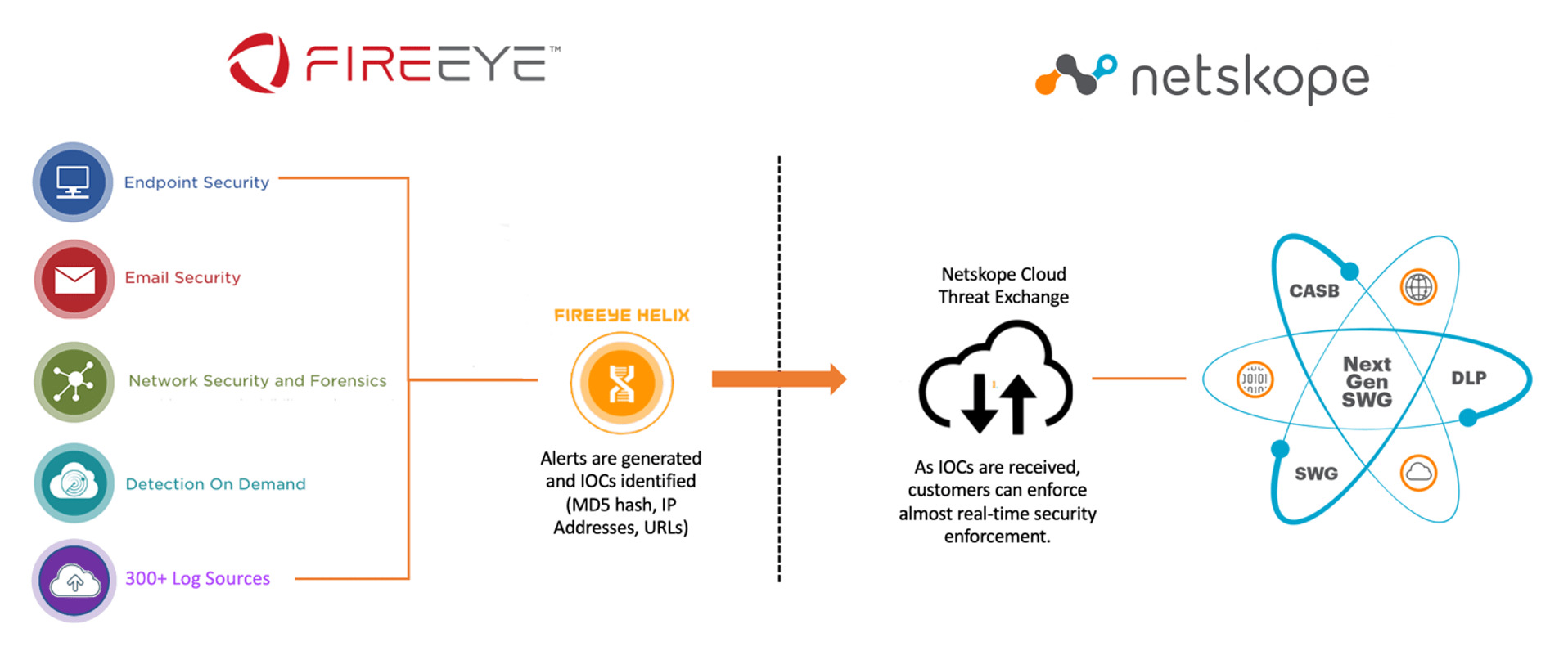
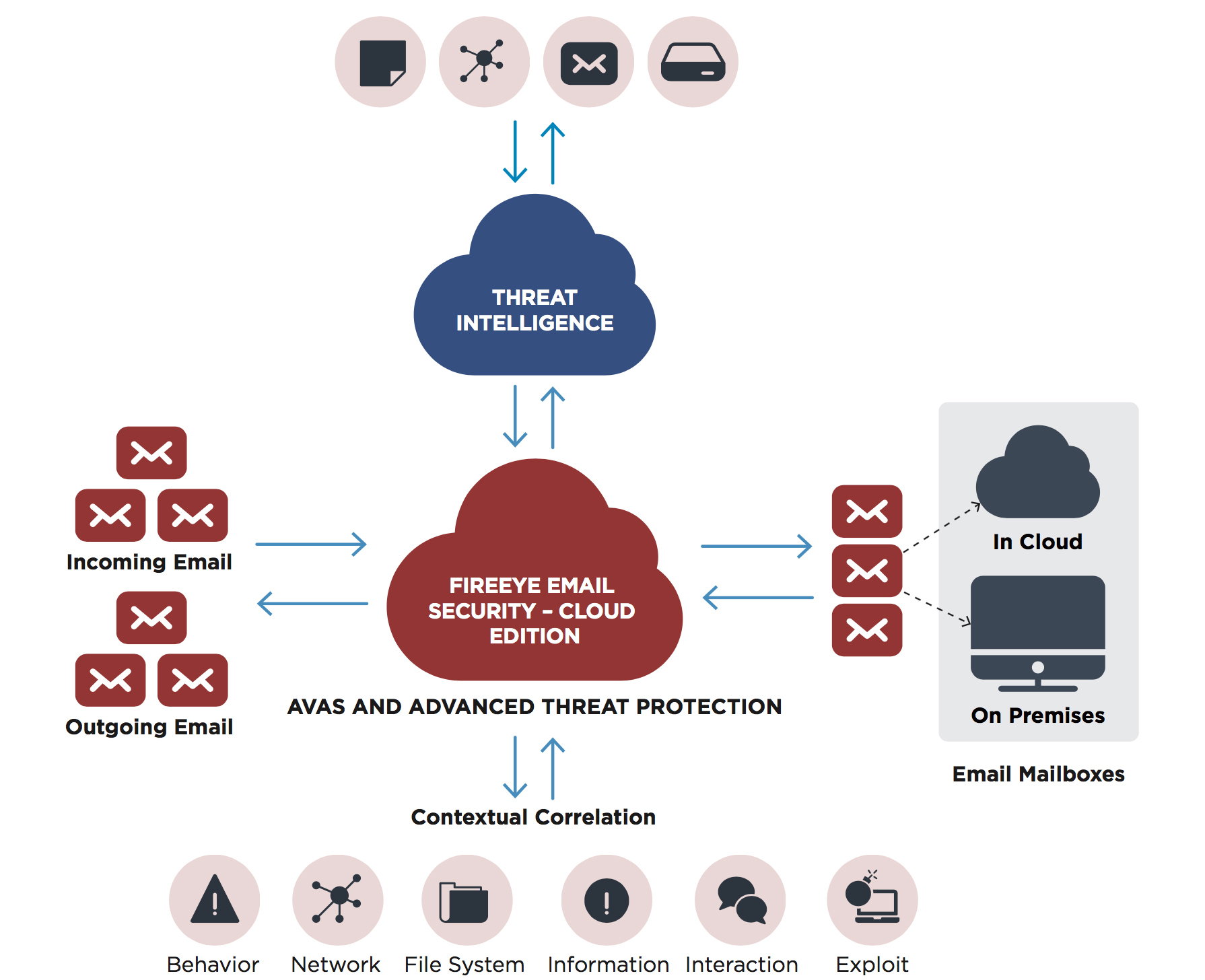
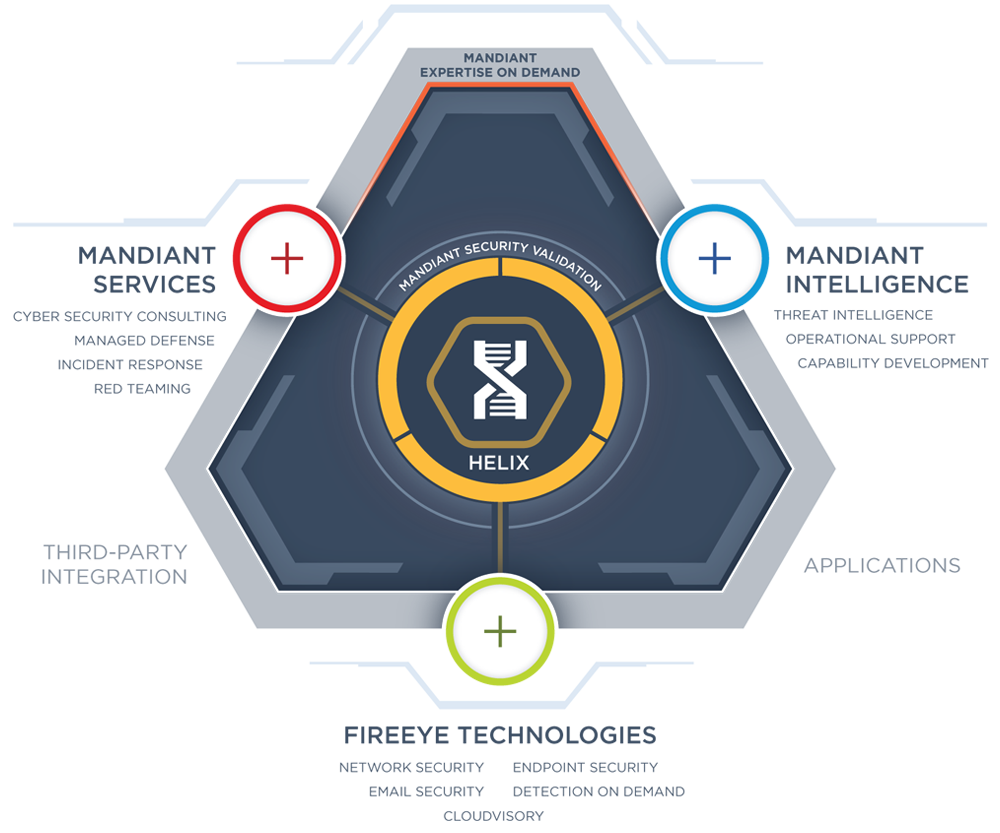
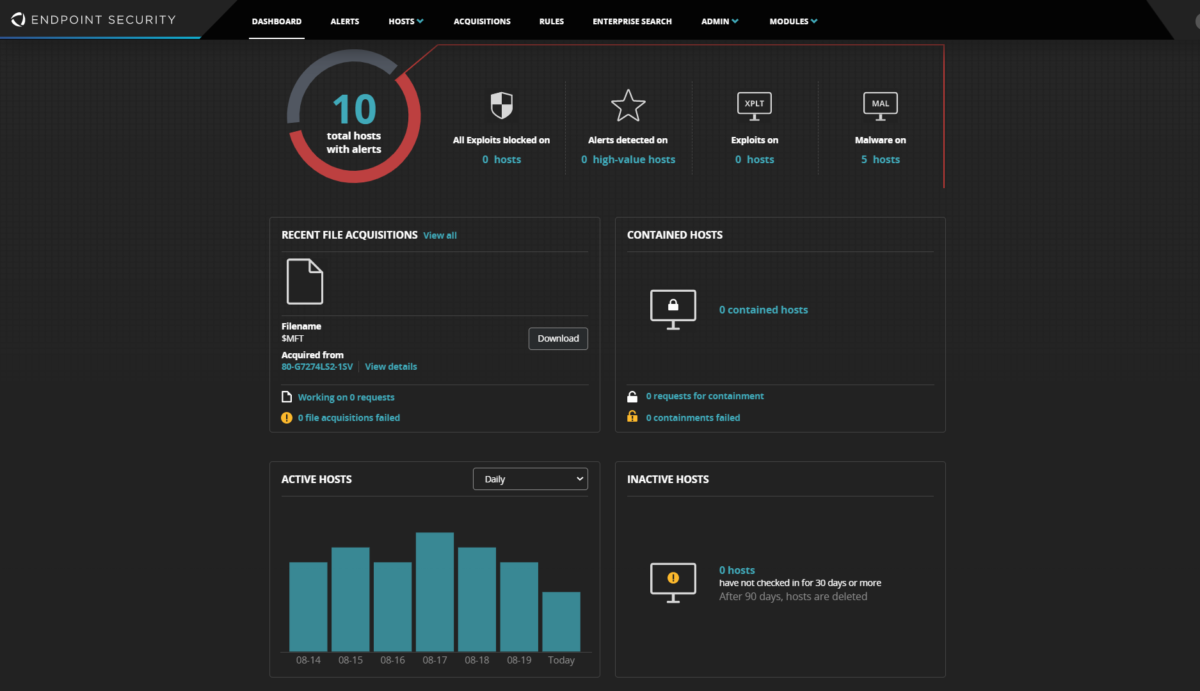
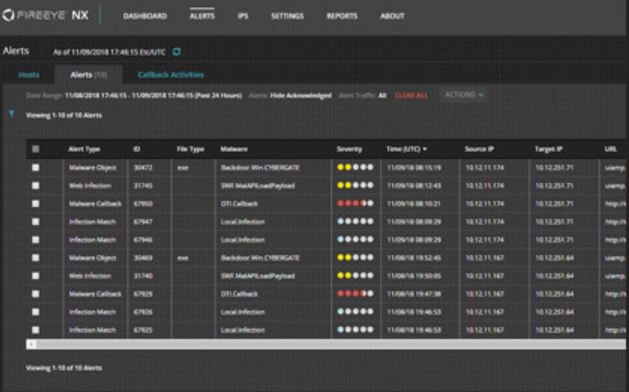
FireEye Helix (Legacy) with On-Premise FireEye Endpoint Security and FireEye Network Security with Packet Capture Deployment Diagram
On-Premise FireEye Endpoint Security, FireEye Network Security, FireEye Email Security, and FireEye File Security with Multi-Vector Virtual Execution Engine Separation and FireEye Malware Analysis Deployment Diagram

FireEye offers proactive OT environment protection with latest cyber physical threat intelligence subscription - IoT Innovator